Enable TLS 1.2 On Exchange Server | Best Practices
PowerShell Script for How To Enable TLS 1.2 in Exchange Server

Table of Contents
How to enable TLS 1.2 for Exchange Server
It is necessary to enable TLS 1.2 on Your Exchange Server to use the best practices.
For better security, you should disable the TLS 1.1 and 1.3 on your Microsoft Exchange Server.
So, if you are using Exchange 2013,16 or Exchange Server 2019, you should enable tls 1.2
In this article, we will learn how to enable tls 1.2 for Exchange Server 2019.
Also, we will know the prerequisites before enabling our tls settings.
Points To Be Considered Before Enabling TLS 1.2
Make sure that, your Domain controller, Global Catalogue Server, and partner application such as SharePoint and Skype for business support TLS 1.2.
Update Windows 7 using Outlook to support TLS 1.2 over WinHttp
Check whether your load balancer, desktop, mobile devices, and browser supports TLS 1.2 or not.
Ensure your third-party application or any custom application integrated with Exchange supports tls 1.2 connection.
Disabling the specific version of TLS will apply to the following functionality.
Connectivity with Outlook Clients (MAPI/HTTP/Outlook Anywhere)
SMTP, POP, IMAP, REST and Autodiscover
OWA, EAC, EWS, and ECP
Use of PowerShell by Exchange over HTTPS
Prerequisites for Enabling TLS 1.2
TLS 1.2 was added to Exchange Server 2013 CU 19, Exchange 2016 CU8
Therefore, Exchange 2019 supports it by default.
As you know, Exchange Server runs on Windows Server, so it is necessary to have the latest updates on your Windows Server for secure TLS installation.
You should also have the latest version of .Net Framework patches supported by CU.
However, if you are running Exchange on old Windows Server 2012 or 2012 R2.
KB3161949 and KB2973337 must be installed before proceeding to enable TLS 1.2
Enabling .Net Framework 4.x Schannel Inheritance
Run the following Cmdlet in elevated PowerShell to enable .net framework 4.x Schannel Inheritance
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319" -Name "SystemDefaultTlsVersions" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319" -Name "SchUseStrongCrypto" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319" -Name "SystemDefaultTlsVersions" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319" -Name "SchUseStrongCrypto" -Value 1 -Type DWord
For .Net Framework 3.5 Schannel Inheritance
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\.NETFramework\v2.0.50727" -Name "SystemDefaultTlsVersions" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\.NETFramework\v2.0.50727" -Name "SchUseStrongCrypto" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727" -Name "SystemDefaultTlsVersions" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727" -Name "SchUseStrongCrypto" -Value 1 -Type DWord
To Enable TLS 1.2 on your server run the following cmdlet on elevated PowerShell
New-Item -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols" -Name "TLS 1.2" -ErrorAction SilentlyContinue
New-Item -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2" -Name "Client" -ErrorAction SilentlyContinue
New-Item -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2" -Name "Server" -ErrorAction SilentlyContinue
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client" -Name "DisabledByDefault" -Value 0 -Type DWord
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client" -Name "Enabled" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server" -Name "DisabledByDefault" -Value 0 -Type DWord
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server" -Name "Enabled" -Value 1 -Type DWord
If you want to disable the TLS 1.2 you can run the following cmdlet.
New-Item -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols" -Name "TLS 1.2" -ErrorAction SilentlyContinue
New-Item -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2" -Name "Client" -ErrorAction SilentlyContinue
New-Item -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2" -Name "Server" -ErrorAction SilentlyContinue
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client" -Name "DisabledByDefault" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client" -Name "Enabled" -Value 0 -Type DWord
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server" -Name "DisabledByDefault" -Value 1 -Type DWord
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server" -Name "Enabled" -Value 0 -Type DWord
Enabling Exchange Server TLS 1.2 via Script
When you want to enable the TLS 1.2 via script.
It is best to check the Exchange Server TLS settings before proceeding.
You can run the Exchange PowerShell Health Checker Script to know the status.
As in our we ran the Exchange Health Checker Script and got the result below.
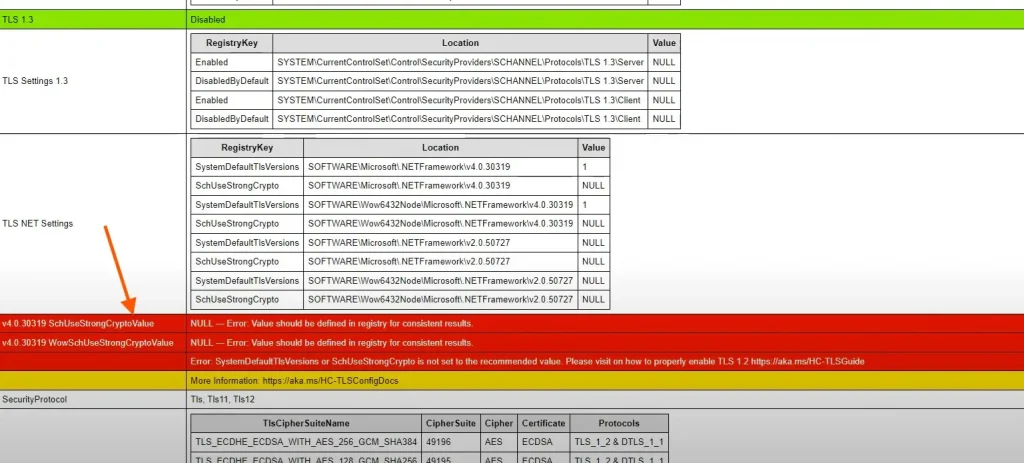
You can see some registry values are not properly set.
PowerShell Script to Enable TLS 1.2 for Exchange Server is available on GitHub
Download the code paste it into a notepad and save it to the file name Set-ExchangeTLS.ps1
In our case, we save this in the script folder inside the C drive.
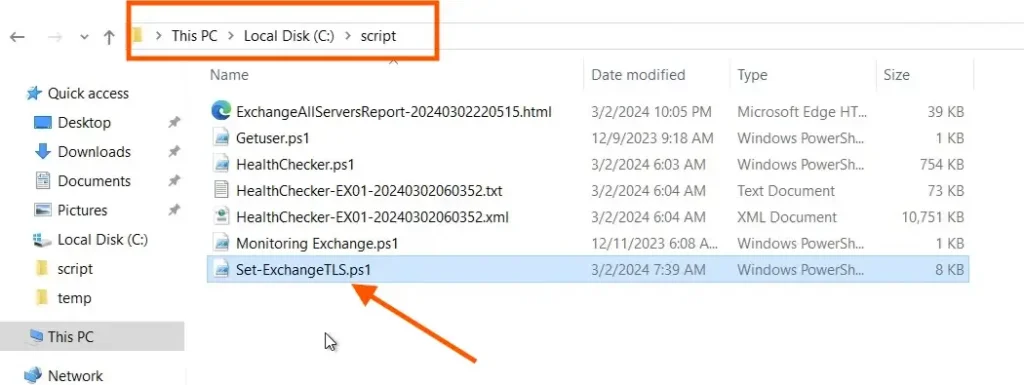
This script will automatically set the registry value for .net 3.5 and 4.x to enable TLS 1,2 and will disable the TLS 1.1
To run the ExchangeTLS PowerShell Script first Open Elevated PowerShell and navigate to the script folder.
Now run the script with the following cmdlet
.\set-ExchangeTLS.ps1Once you run the above script, you will get the results below.
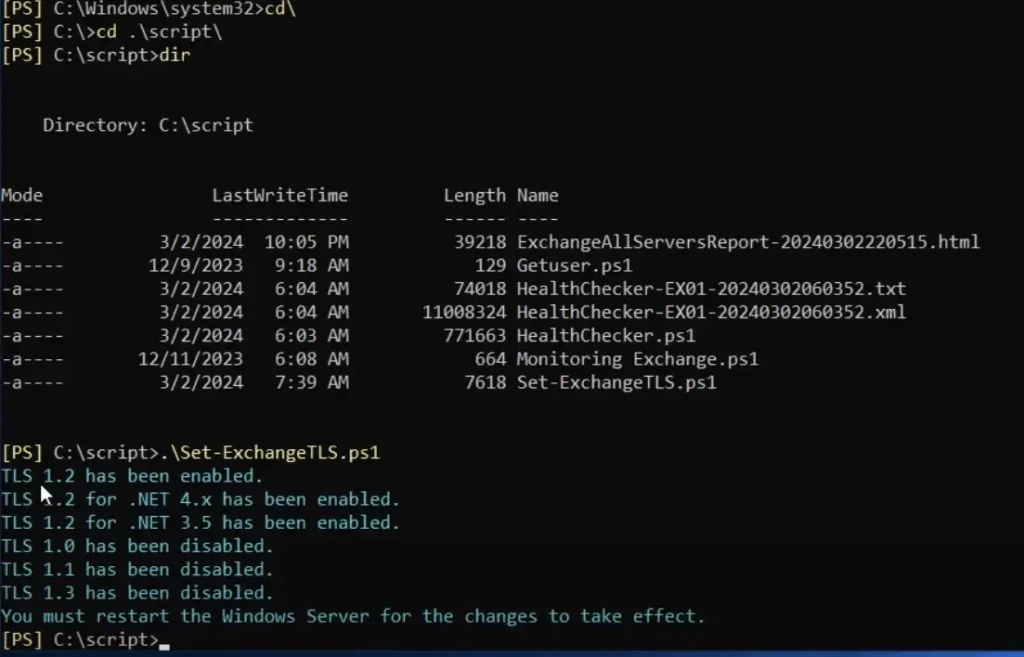
After running the script, restart the computer.
Verifying the Exchange Server TLS Settings
As we already followed the steps to configure TLS 1.2 on our Exchange Server by following the best practices.
Now it’s time to check and verify the Exchange Server TLS settings.
We will again run the Exchange Health Checker script and will generate the HTML report.
Now you will see that all the errors are gone and we successfully configured TLS 1.2 on our Exchange Server.
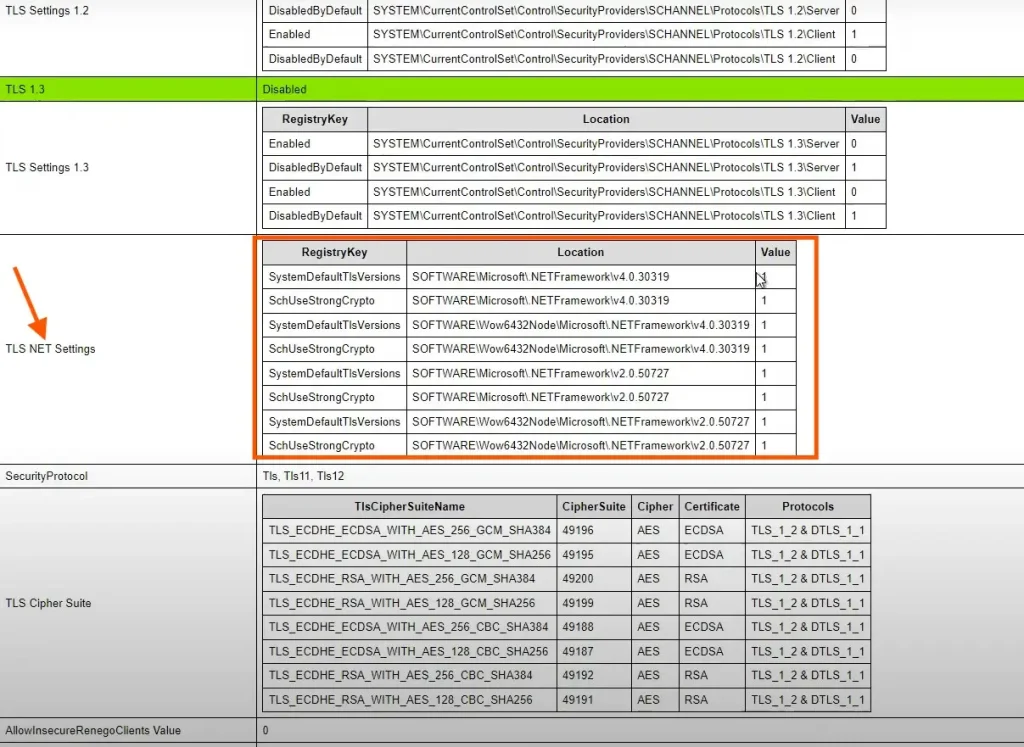
Conclusion
So, we learned how to configure TLS 1.2 for Exchange Server 2019. You should configure it for all versions if you are running Exchange 2013,2016 or 2019.
Microsoft recommends to all Exchange organizations to enable TLS 1.2 for best practices implementation in the Exchange Server.
Therefore, it helps to secure your Exchange Server.
You may also like more Exchange Server Tutorials
Watch the below video for configuring TLS 1.2 on Exchange Server 2019




